¶ Como Cadastrar o Concentrador Juniper no HubSoft
Antes de prosseguir, é preciso determinar se o seu equipamento possui a licença Service-DC. Esta licença é necessária para se utilizar controle de banda dinâmico no equipamento. Caso contrário é necessário cadastrar no Juniper todos os profiles de navegação que o seu provedor comercializa.
Para cadastrar o concentrador Juniper no Hubsoft, primeiramente é necessário cadastrá-lo adequadamente no sistema. Posteriormente é necessário ajustar as configurações do NAS de acordo com o tipo de licença que você possui.
¶ Configurar no HubSoft
Para configurar o concentrador no HubSoft, devemos seguir algumas etapas, como:
¶ Cadastrar Pontos de Presença
Primeiramente deve-se cadastrar o POP de Conexão, para cadastrar acesse o menu Rede > Pontos de Presença
No canto superior direito, clique em Adicionar
Na aba Geral digite o Nome do seu POP
Na aba Endereço digite o endereço do seu POP
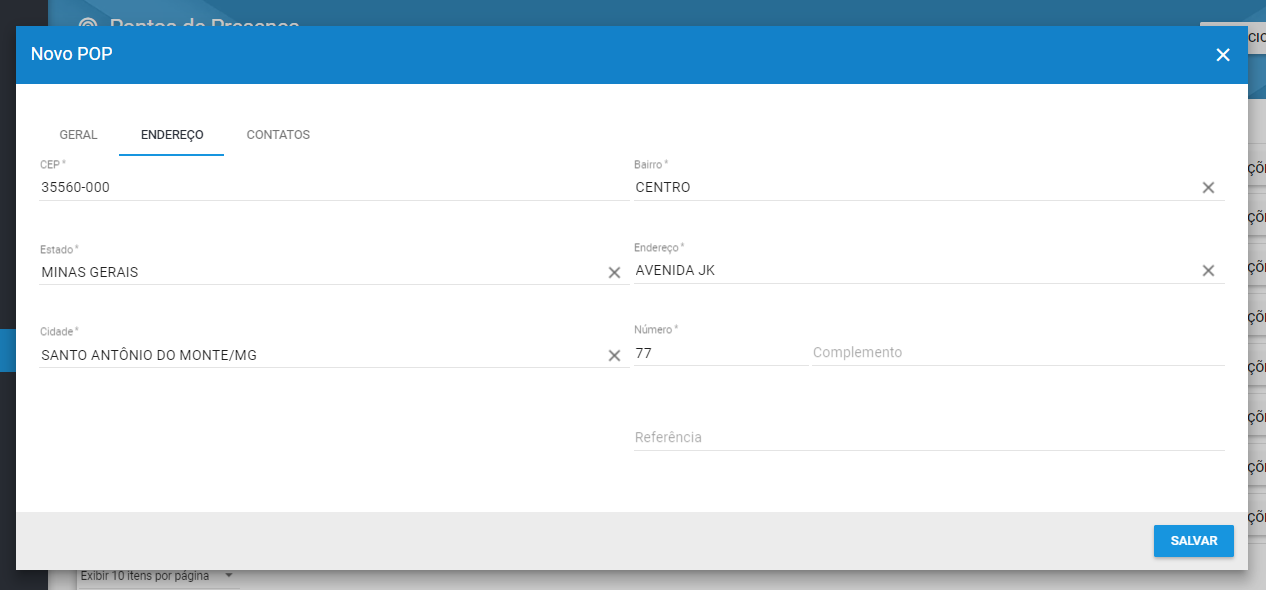
A aba Contatos é opcional, para caso você queira adicionar um contato para seu POP, clique em Salvar
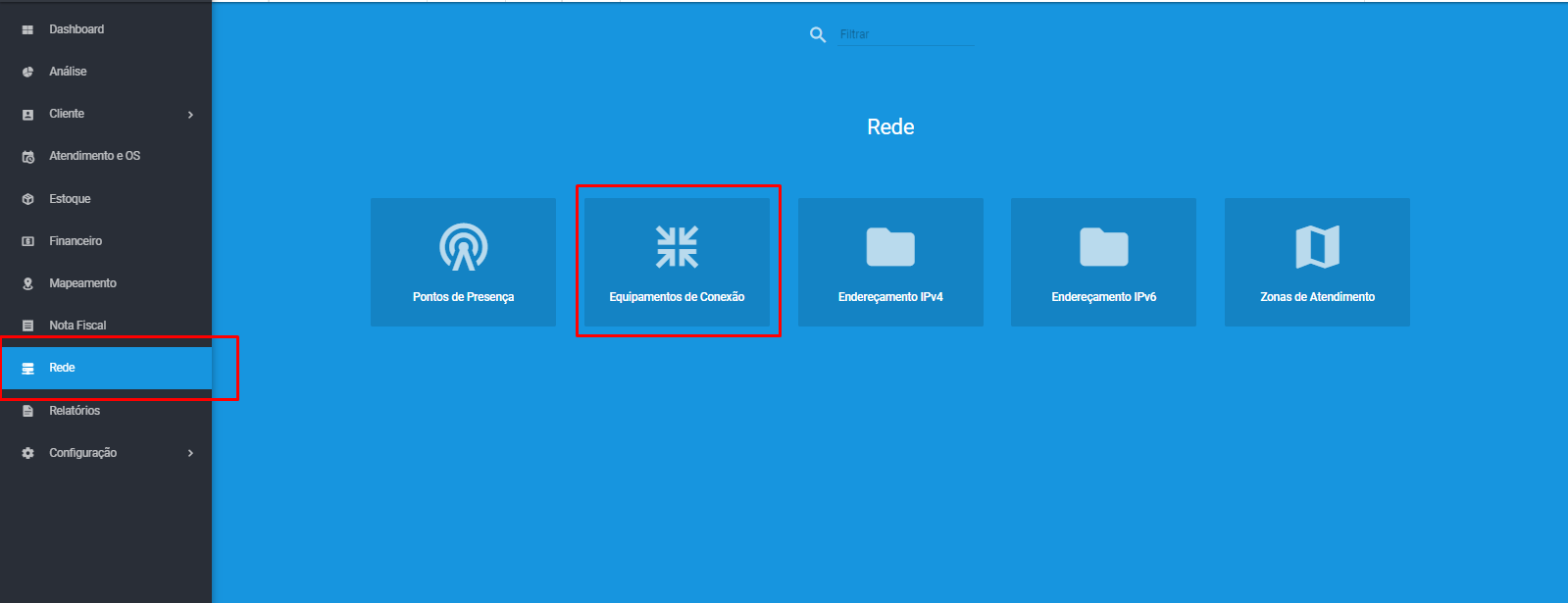
¶ Cadastrar Equipamentos de Conexão
Agora devemos cadastrar o ‘Equipamento de Conexão’, para cadastrar vá em “Rede > Equipamentos de Conexão”
No canto superior direito, clique em “+”
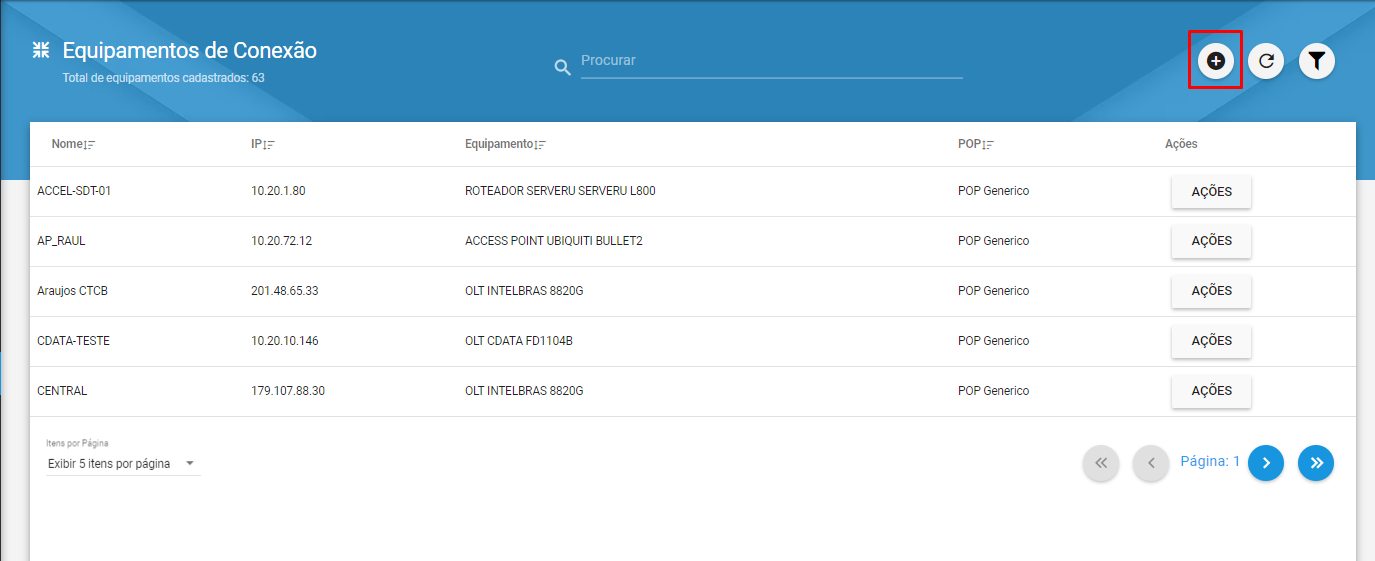
Preencha os dados do Equipamento:
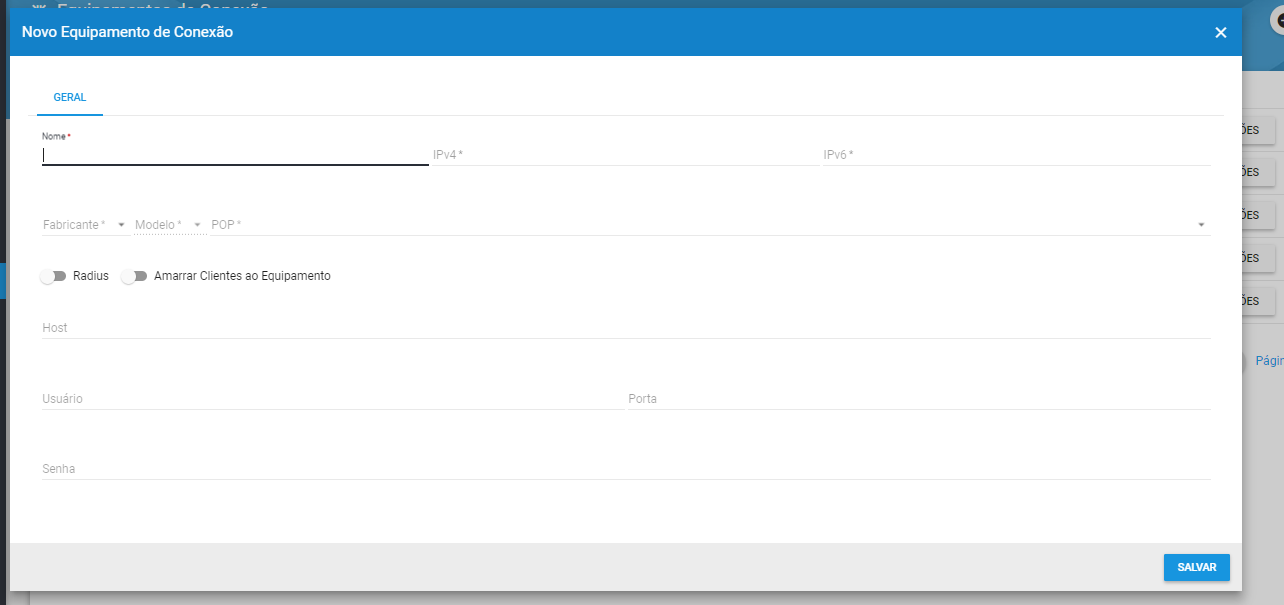
Cadastrando um Novo Equipamento de Conexão:
- Nome: Nome da sua preferencia
- IPv4 ou IPv6: O IP do seu equipamento
- Fabricante: Escolha o Juniper
- Modelo: Escolha o modelo referente ao seu cenário: MX5, MX10, MX80, etc
- POP: Escolha o POP que você criou
- Marque a chave do Radius, escolha o Radius, digite o Secret e a Porta Incoming (Secret e a Porta Incoming deve ser a mesma cadastrada no concentrador)
- Escolha o Tipo de NAS como Juniper caso possua a licença “service-dc”, caso contrário selecione Juniper-Static
- Digite o Usuário como hubsoft, digite a Senha e a Porta do SSH
- Clique em Salvar
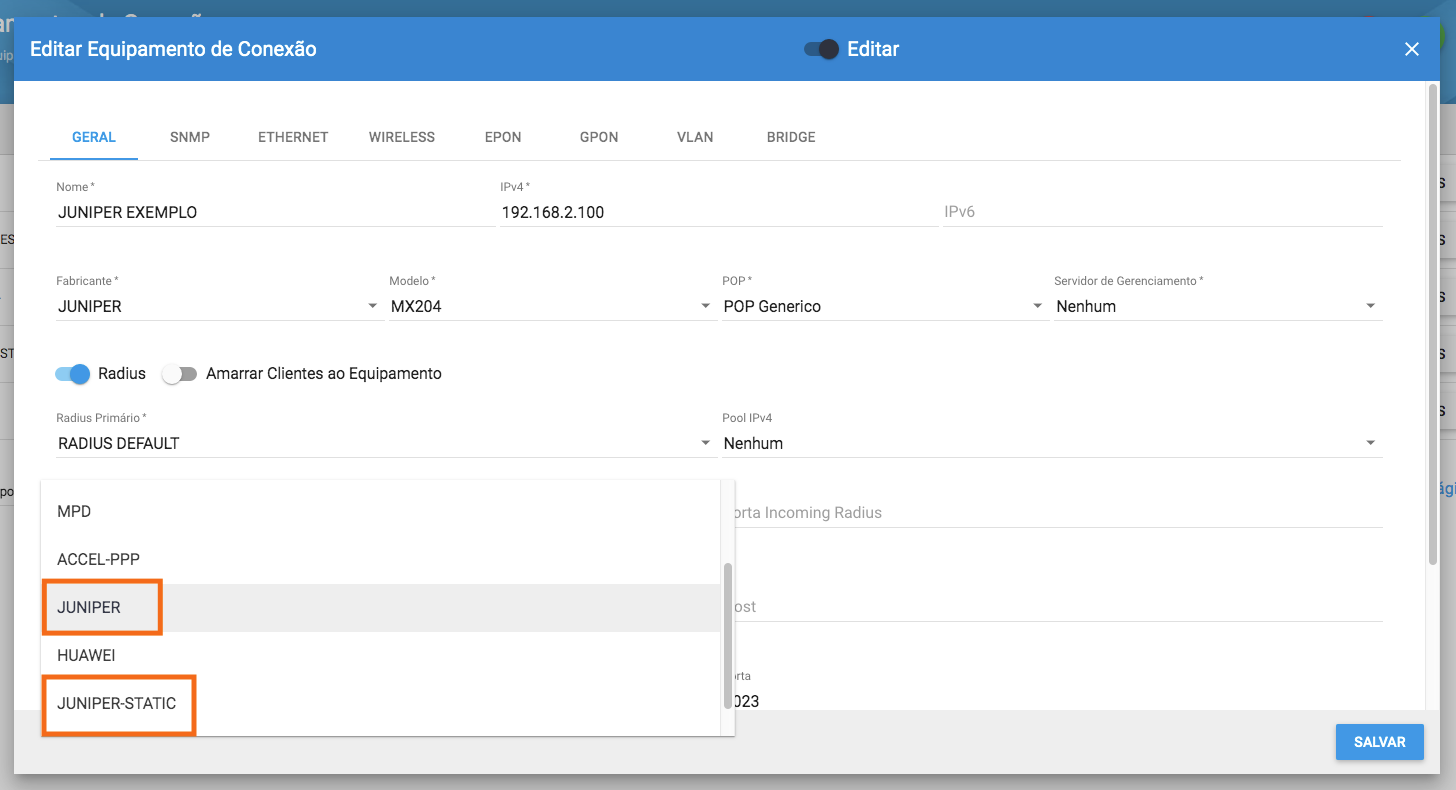
¶ Exemplo de configuração para concentrador Juniper
¶ Determinando se a licença “Service-DC” está instalada no equipamento
Para verificar se o seu equipamento possui a licença instalada, basta executar o seguinte comando:
show system license
License usage:
Licenses Licenses Licenses Expiry
Feature name used installed needed
subscriber-accounting 1 1 0 permanent
subscriber-authentication 0 1 0 permanent
subscriber-address-assignment 1 1 0 permanent
subscriber-vlan 0 1 0 permanent
subscriber-ip 0 1 0 permanent
service-dc 0 1 0 permanent
service-accounting 0 1 0 permanent
service-qos 0 1 0 permanent
service-ancp 0 1 0 permanent
service-cbsp 0 1 0 permanent
scale-subscriber 1322 8000 0 permanent
scale-l2tp 0 1000 0 permanent
scale-mobile-ip 0 1000 0 permanent
l2tp-inline-lns 0 1 0 permanent
Nesse caso, é possível ver que o equipamento em questão possui a licença. Caso a linha referente à licença não esteja aparecendo, o equipamento não possui a licença.
¶ Exemplo de configuração com licença service-dc
Neste caso selecione o Tipo de NAS no Hubsoft como Juniper
ATIVA O VERSIONAMENTO DA CAIXA:
set system dynamic-profile-options versioning
Para configuração de equipamentos utilizando a licença service-dc, o único requisito, além das configurações básicas, é possuir o profile do Hubsoft criado:
set dynamic-profiles Hubsoft-Rate-Limit variables up-rate default-value 32k
set dynamic-profiles Hubsoft-Rate-Limit variables up-rate mandatory
set dynamic-profiles Hubsoft-Rate-Limit variables down-rate default-value 32k
set dynamic-profiles Hubsoft-Rate-Limit variables down-rate mandatory
set dynamic-profiles Hubsoft-Rate-Limit variables filter-up uid
set dynamic-profiles Hubsoft-Rate-Limit variables filter-down uid
set dynamic-profiles Hubsoft-Rate-Limit variables filter-ipv6-up uid
set dynamic-profiles Hubsoft-Rate-Limit variables filter-ipv6-down uid
set dynamic-profiles Hubsoft-Rate-Limit variables shaper-up uid
set dynamic-profiles Hubsoft-Rate-Limit variables shaper-down uid
set dynamic-profiles Hubsoft-Rate-Limit interfaces "$junos-interface-ifd-name" unit "$junos-interface-unit" family inet filter input "$filter-up"
set dynamic-profiles Hubsoft-Rate-Limit interfaces "$junos-interface-ifd-name" unit "$junos-interface-unit" family inet filter output "$filter-down"
set dynamic-profiles Hubsoft-Rate-Limit interfaces "$junos-interface-ifd-name" unit "$junos-interface-unit" family inet6 filter input "$filter-ipv6-up"
set dynamic-profiles Hubsoft-Rate-Limit interfaces "$junos-interface-ifd-name" unit "$junos-interface-unit" family inet6 filter output "$filter-ipv6-down"
set dynamic-profiles Hubsoft-Rate-Limit firewall family inet filter "$filter-down" interface-specific
set dynamic-profiles Hubsoft-Rate-Limit firewall family inet filter "$filter-down" term accept then policer "$shaper-down"
set dynamic-profiles Hubsoft-Rate-Limit firewall family inet filter "$filter-down" term accept then service-filter-hit
set dynamic-profiles Hubsoft-Rate-Limit firewall family inet filter "$filter-down" term accept then accept
set dynamic-profiles Hubsoft-Rate-Limit firewall family inet filter "$filter-up" interface-specific
set dynamic-profiles Hubsoft-Rate-Limit firewall family inet filter "$filter-up" term accept then policer "$shaper-up"
set dynamic-profiles Hubsoft-Rate-Limit firewall family inet filter "$filter-up" term accept then service-filter-hit
set dynamic-profiles Hubsoft-Rate-Limit firewall family inet filter "$filter-up" term accept then accept
set dynamic-profiles Hubsoft-Rate-Limit firewall family inet6 filter "$filter-ipv6-up" interface-specific
set dynamic-profiles Hubsoft-Rate-Limit firewall family inet6 filter "$filter-ipv6-up" term accept then policer "$shaper-up"
set dynamic-profiles Hubsoft-Rate-Limit firewall family inet6 filter "$filter-ipv6-up" term accept then service-filter-hit
set dynamic-profiles Hubsoft-Rate-Limit firewall family inet6 filter "$filter-ipv6-up" term accept then accept
set dynamic-profiles Hubsoft-Rate-Limit firewall family inet6 filter "$filter-ipv6-down" interface-specific
set dynamic-profiles Hubsoft-Rate-Limit firewall family inet6 filter "$filter-ipv6-down" term accept then policer "$shaper-down"
set dynamic-profiles Hubsoft-Rate-Limit firewall family inet6 filter "$filter-ipv6-down" term accept then service-filter-hit
set dynamic-profiles Hubsoft-Rate-Limit firewall family inet6 filter "$filter-ipv6-down" term accept then accept
set dynamic-profiles Hubsoft-Rate-Limit firewall policer "$shaper-up" filter-specific
set dynamic-profiles Hubsoft-Rate-Limit firewall policer "$shaper-up" logical-interface-policer
set dynamic-profiles Hubsoft-Rate-Limit firewall policer "$shaper-up" if-exceeding bandwidth-limit "$up-rate"
set dynamic-profiles Hubsoft-Rate-Limit firewall policer "$shaper-up" if-exceeding burst-size-limit 1024000000
set dynamic-profiles Hubsoft-Rate-Limit firewall policer "$shaper-up" then discard
set dynamic-profiles Hubsoft-Rate-Limit firewall policer "$shaper-down" filter-specific
set dynamic-profiles Hubsoft-Rate-Limit firewall policer "$shaper-down" logical-interface-policer
set dynamic-profiles Hubsoft-Rate-Limit firewall policer "$shaper-down" if-exceeding bandwidth-limit "$down-rate"
set dynamic-profiles Hubsoft-Rate-Limit firewall policer "$shaper-down" if-exceeding burst-size-limit 1024000000
set dynamic-profiles Hubsoft-Rate-Limit firewall policer "$shaper-down" then discard
Caso deseje utilizar CGNAT, o filtro $filter-up pode ser modificado de forma a redirecionar os clientes para o equipamento responsável por aplicar o NAT, conforme abaixo:
Além do dynamic-profile Hubsoft-Rate-Limit, também é necessário criar um dynamic-profile que será vinculados às interfaces que receberão as requisições PPPoE:
set dynamic-profiles PPPoE-Base routing-instances "$junos-routing-instance" interface "$junos-interface-name"
set dynamic-profiles PPPoE-Base routing-instances "$junos-routing-instance" routing-options access route $junos-framed-route-ip-address-prefix next-hop "$junos-framed-route-nexthop"
set dynamic-profiles PPPoE-Base routing-instances "$junos-routing-instance" routing-options access-internal route $junos-subscriber-ip-address qualified-next-hop "$junos-interface-name"
set dynamic-profiles PPPoE-Base interfaces pp0 unit "$junos-interface-unit" ppp-options chap
set dynamic-profiles PPPoE-Base interfaces pp0 unit "$junos-interface-unit" ppp-options pap
set dynamic-profiles PPPoE-Base interfaces pp0 unit "$junos-interface-unit" ppp-options mru 1480
set dynamic-profiles PPPoE-Base interfaces pp0 unit "$junos-interface-unit" ppp-options mtu 1480
set dynamic-profiles PPPoE-Base interfaces pp0 unit "$junos-interface-unit" pppoe-options underlying-interface "$junos-underlying-interface"
set dynamic-profiles PPPoE-Base interfaces pp0 unit "$junos-interface-unit" pppoe-options server
set dynamic-profiles PPPoE-Base interfaces pp0 unit "$junos-interface-unit" keepalives interval 60
set dynamic-profiles PPPoE-Base interfaces pp0 unit "$junos-interface-unit" family inet rpf-check
set dynamic-profiles PPPoE-Base interfaces pp0 unit "$junos-interface-unit" family inet filter input "$junos-input-filter"
set dynamic-profiles PPPoE-Base interfaces pp0 unit "$junos-interface-unit" family inet filter output "$junos-output-filter"
set dynamic-profiles PPPoE-Base interfaces pp0 unit "$junos-interface-unit" family inet unnumbered-address "$junos-loopback-interface"
set dynamic-profiles PPPoE-Base interfaces pp0 unit "$junos-interface-unit" family inet6 filter input "$junos-input-ipv6-filter"
set dynamic-profiles PPPoE-Base interfaces pp0 unit "$junos-interface-unit" family inet6 filter output "$junos-output-ipv6-filter"
set dynamic-profiles PPPoE-Base interfaces pp0 unit "$junos-interface-unit" family inet6 unnumbered-address "$junos-loopback-interface"
set dynamic-profiles PPPoE-Base protocols router-advertisement interface "$junos-interface-name" prefix $junos-ipv6-ndra-prefix
¶ Configuração do filtro de entrada
set dynamic-profiles Hubsoft-Rate-Limit firewall family inet filter "$filter-up" interface-specific
set dynamic-profiles Hubsoft-Rate-Limit firewall family inet filter "$filter-up" term SHAPER then policer "$shaper-up"
set dynamic-profiles Hubsoft-Rate-Limit firewall family inet filter "$filter-up" term SHAPER then next term
set dynamic-profiles Hubsoft-Rate-Limit firewall family inet filter "$filter-up" term CGNAT from source-address 100.64.0.0/10
set dynamic-profiles Hubsoft-Rate-Limit firewall family inet filter "$filter-up" term CGNAT then routing-instance CGNAT
set dynamic-profiles Hubsoft-Rate-Limit firewall family inet filter "$filter-up" term accept then accept
¶ Configuração da Routing-Instance
set routing-instances CGNAT instance-type forwarding
set routing-instances CGNAT routing-options static route 0.0.0.0/0 next-hop A.B.C.D
¶ Ajustes para funcionamento correto da routing-instance
set routing-options rib-groups INTERFACE-GROUP import-rib inet.0
set routing-options rib-groups INTERFACE-GROUP import-rib CGNAT.inet.0
¶ Exemplo de configuração sem a licença service-dc
Neste caso selecione o Tipo de NAS como Juniper-Static no Hubsoft
Quando não se possui a licença Service-DC e o Tipo de NAS Juniper-Static é utilizado, é necessário criar os profiles de banda no Juniper de acordo com as configurações de navegação do serviço no Hubsoft.
¶ Configurações de navegação do Serviço no Hubsoft:
Para casos em que o controle de banda é estático dentro do Juniper, é preciso criar esse controle para cada plano explicado. Para isso, tem que se identificar a velocidade de download e upload do serviço. Clicando em Configuração > Geral > Planos / Serviços.
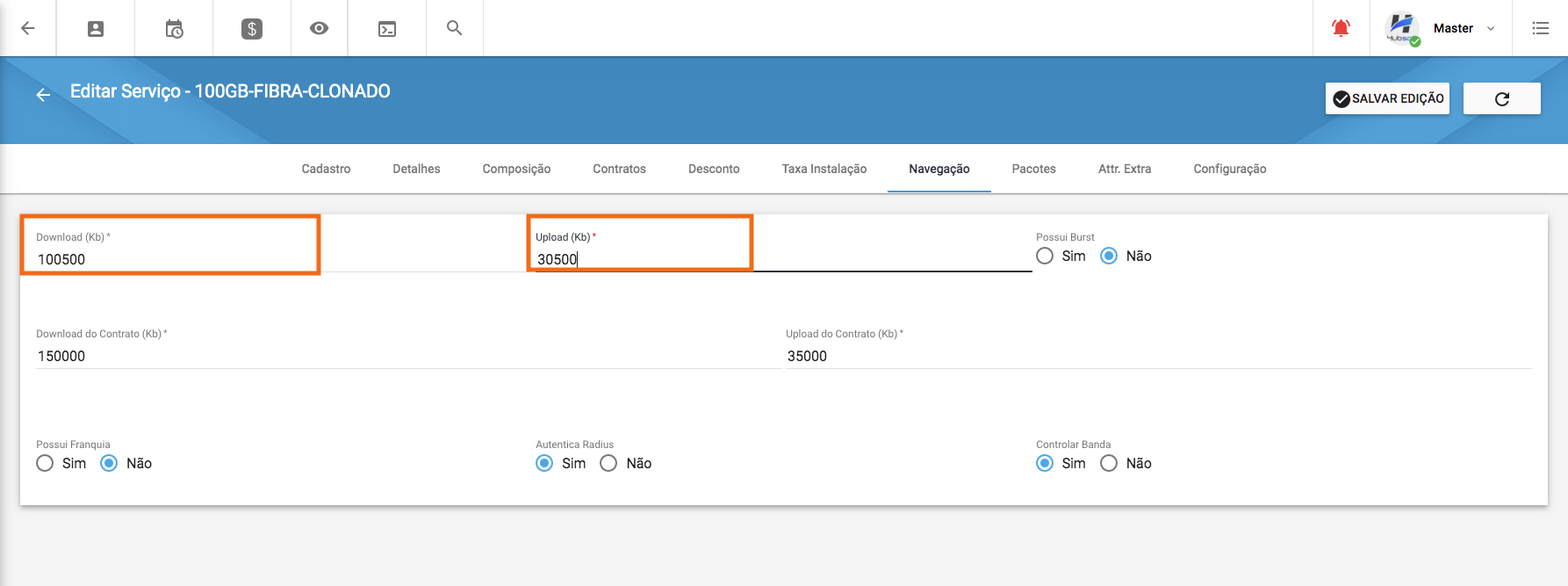
Tomando como exemplo o serviço da imagem acima, os seguintes filtros devem ser criados no Juniper:
Download IPv4: HUBSOFT-PROFILE-100500-DOWN
Upload IPv4: HUBSOFT-PROFILE-30500-UP
Download IPv6: HUBSOFT-PROFILE-V6-100500-DOWN
Upload IPv6: HUBSOFT-PROFILE-V6-30500-UP
Logo, as queues criadas no Juniper ficaram parecidas com o padrão abaixo:
set firewall family inet filter HUBSOFT-PROFILE-100500-DOWN interface-specific
set firewall family inet filter HUBSOFT-PROFILE-100500-DOWN term 10 then policer POLICER-100500
set firewall family inet filter HUBSOFT-PROFILE-100500-DOWN term 20 then accept
set firewall family inet filter HUBSOFT-PROFILE-V6-100500-DOWN interface-specific
set firewall family inet filter HUBSOFT-PROFILE-V6-100500-DOWN term 10 then policer POLICER-100500
set firewall family inet filter HUBSOFT-PROFILE-V6-100500-DOWN term 20 then accept
set firewall family inet filter HUBSOFT-PROFILE-30500-UP interface-specific
set firewall family inet filter HUBSOFT-PROFILE-30500-UP term 10 then policer POLICER-30500
set firewall family inet filter HUBSOFT-PROFILE-30500-UP term 20 then accept
set firewall family inet filter HUBSOFT-PROFILE-V6-30500-UP interface-specific
set firewall family inet filter HUBSOFT-PROFILE-V6-30500-UP term 10 then policer POLICER-30500
set firewall family inet filter HUBSOFT-PROFILE-V6-30500-UP term 20 then accept
set firewall policer POLICER-100500 logical-interface-policer
set firewall policer POLICER-100500 if-exceeding bandwidth-limit 100500k
set firewall policer POLICER-100500 if-exceeding burst-size-limit 32k
set firewall policer POLICER-100500 then discard
set firewall policer POLICER-30500 logical-interface-policer
set firewall policer POLICER-30500 if-exceeding bandwidth-limit 30500k
set firewall policer POLICER-30500 if-exceeding burst-size-limit 16k
set firewall policer POLICER-30500 then discard
¶ Configurações recomendadas do servidor Radius no Juniper
Aqui são algumas boas práticas nos camandos do Juniper com relação ao radius.
¶ Configurações do Radius:
set access radius-server A.B.C.D port 1812
set access radius-server A.B.C.D accounting-port 1813
set access radius-server A.B.C.D secret "$9$tiavu1hLX-dwgM8aUji.muOBIyl"
set access radius-server A.B.C.D timeout 40
set access radius-server A.B.C.D retry 3
set access radius-server A.B.C.D accounting-timeout 20
set access radius-server A.B.C.D accounting-retry 6
set access radius-server A.B.C.D source-address 10.28.33.20
set access radius-disconnect-port 3799
set access radius-disconnect [[IP-RADIUS-SERVER]] secret [[SECRET-RADIUS]]
¶ Configurações do Access-Profile:
Aqui vamos verificar algumas configurações referentes ao Access-Profile no Juniper.
PROFILE USADO PARA CONFIGURAÇÃO ESTÁTICA, QUANDO NÃO TEM A LICENÇA
set access profile PPPoE-Access-Profile accounting-order radius
set access profile PPPoE-Access-Profile authentication-order radius
set access profile PPPoE-Access-Profile domain-name-server-inet A.B.C.D
set access profile PPPoE-Access-Profile domain-name-server-inet A.B.C.D
set access profile PPPoE-Access-Profile radius authentication-server A.B.C.D
set access profile PPPoE-Access-Profile radius accounting-server A.B.C.D
set access profile PPPoE-Access-Profile radius options nas-identifier 4
set access profile PPPoE-Access-Profile radius options nas-port-id-delimiter "%"
set access profile PPPoE-Access-Profile radius options nas-port-id-format nas-identifier
set access profile PPPoE-Access-Profile radius options nas-port-id-format interface-description
set access profile PPPoE-Access-Profile radius options nas-port-type ethernet ethernet
set access profile PPPoE-Access-Profile radius options calling-station-id-delimiter :
set access profile PPPoE-Access-Profile radius options calling-station-id-format mac-address
set access profile PPPoE-Access-Profile radius options accounting-session-id-format decimal
set access profile PPPoE-Access-Profile radius options client-authentication-algorithm direct
set access profile PPPoE-Access-Profile radius options client-accounting-algorithm direct
set access profile PPPoE-Access-Profile radius options service-activation dynamic-profile required-at-login
set access profile PPPoE-Access-Profile accounting order radius
set access profile PPPoE-Access-Profile accounting coa-immediate-update
set access profile PPPoE-Access-Profile accounting update-interval 10
set access profile PPPoE-Access-Profile accounting statistics volume-time
¶ Depuração de problemas de autenticação
Podem existir algumas falhas na configuração que impeçam o funcionamento correto da autenticação dos assinantes. Alguns dos principais motivos:
-
Falta da licença service-dc ao utilizar controle de banda dinâmico, ou esquecer de reiniciar o roteador após aplicar a licença
-
Esquecer de habilitar o suporte a gerenciamento de assinantes (set system services subscriber-management enable) e reiniciar o equipamento após habilitar
-
Esquecer de configurar os IPs na Loopback (lo0) do Juniper, tanto para IPv4 quanto para IPv6, caso esteja em uso
-
Esquecer de criar os filtros para controle de banda estático (set firewall family inet filter …)
-
Esquecer de criar o profile Hubsoft-Rate-Limit ao utilizar controle de banda dinâmico
-
Verificar se o IP de loopback não está atribuído em outra interface física
Caso o problema persista, alguns logs podem ser úteis para a depuração de problemas:
set system processes general-authentication-service traceoptions file auth-geral.log
set system processes general-authentication-service traceoptions file size 10m
set system processes general-authentication-service traceoptions file files 4
set system processes general-authentication-service traceoptions file world-readable
set system processes general-authentication-service traceoptions flag all
set system processes general-authentication-service traceoptions flag user-access
set system processes general-authentication-service traceoptions flag address-assignment
set system processes general-authentication-service traceoptions flag radius
set system processes general-authentication-service traceoptions flag framework
set system processes smg-service traceoptions level verbose
set system processes smg-service traceoptions flag all
¶ Com os dois logs acima habilitados, é possível analisar os seguintes arquivos em busca de falhas
show log auth-geral.log | match reason
show log bbesmgd | match fail
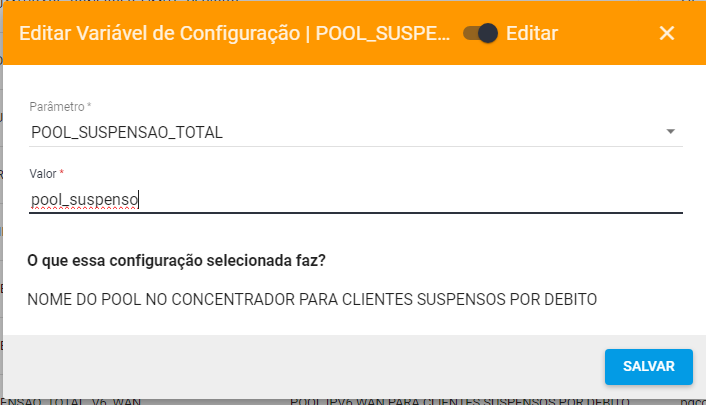
¶ Configurar pool de suspensão Juniper
- Configurar pool suspensão v4:
set access address-assignment pool pool_suspenso family inet network 10.0.0.0/24
- Configurar pool suspensão v6:
set access address-assignment pool poolv6-suspenso family inet6 prefix FC00:0000:0000::/40
set access address-assignment pool poolv6-suspenso family inet6 range poolv6-suspenso prefix-length 56
Após a criação dos pools, basta ajustar as regras de drop no firewall e adicionar a variável dentro do sistema em:
Configuração -> Geral -> Variáveis
Adicionar as seguintes chaves:
- POOL_SUSPENSAO_TOTAL -> Para IPv4
- POOL_SUSPENSAO_TOTAL_V6_LAN -> Para IPv6
No valor de cada chave basta adicionar o nome do pool que criou.